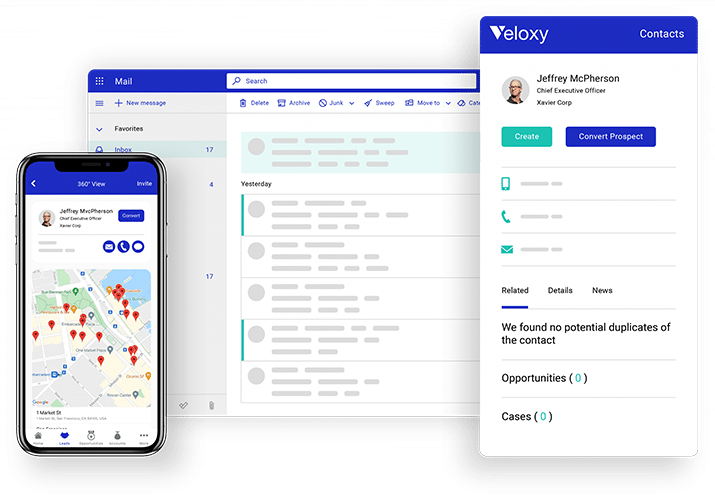
TRUST. PRIVACY. PEACE OF MIND.
Veloxy Security
We apply hundreds of security processes and controls to help protect your data, applications, systems, and networks.

Trusted by Thousands.
We invite you to see why thousands of salespeople, IT professionals, and organizations trust us with their data, privacy, devices, communication, and Salesforce instance.



Trusted by Applications.
We developed a privacy friendly sales software that meets the strictest compliance and security guidelines for today’s most popular business communication and data applications.





Security Built on Trust.
Security is built into every feature and every application. Our processes and controls help us comply with the most sought-after and acceptable standards, regulations, and certifications.
We take security seriously.
Every person and team using Veloxy expects their data to be secure and confidential. We understand how important the responsibility of safeguarding this data is to our customers to maintain that trust.
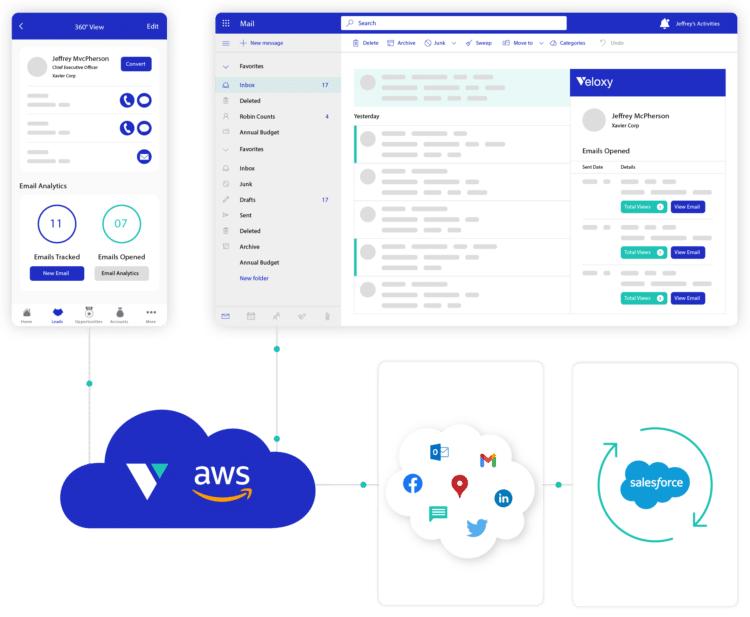
Veloxy is built on latest cloud-based architecture using industry standard services and technologies. Veloxy is hosted in Amazon AWS secure private cloud. You can see more details about Amazon AWS security here
Veloxy successfully passed comprehensive security review by Salesforce and we are Salesforce certified ISV partner. You can see more details about Salesforce Security Review here. Veloxy is a Salesforce white listed app and it is available in AppExchange.
Check all of the boxes.
If you’re looking for all of the necessary information for checking all of the boxes, download and print out our full security details.
Your Data is Protected.
Security is built into every feature and every application. Our processes and controls help us comply with the most sought-after and acceptable standards, regulations, and certifications.
We take data protection seriously.
Every person and team using Veloxy expects their data to be secure and confidential.
- Encrypted Sessions
- Strong Authentication
- Oauth 2.0 Client Access Protocols
- Source Code Hardening
- Clean Data Principles
- Multi Layered Security Credentials
- AWS Load Balancer Secure Endpoint
- IP Address Range Lockdown
- API Access Keys
- Certificate Verification
- Secure Access and Activity Log
- Transient URLs

Privacy Matters.
If you’re looking for all of the necessary information for checking all of the boxes, download and print out our full security details.
Security FAQ.
Security is built into every feature and every application. Our processes and controls help us comply with the most sought-after and acceptable standards, regulations, and certifications.