Security Details
Overview of Company & Product
Veloxy, a Top 50 Sales Software according to G2, is one of the world’s leading
platform’s for field sales software, Salesforce automation, sales engagement,
AI sales assistant software, and sales analytics.
Since 2015, Veloxy has been on a mission to extend, automate, and intelligently
prioritize activities tied to Salesforce. Today, thousands of salespeople across the
globe use Veloxy to maximize their sales productivity and efficiency, thereby
generating more revenue and eliminating time-waste for their organization.
The Veloxy products are Software-as-a-Service applications. These apps are
accessible as a web-application, inbox extension or plug-in, and smartphone
application.
Our Commitment to Security & Your Data
Veloxy’s commitment to security and protecting your data is all about giving you
peace of mind. We’ve invested in the necessary security resources, controls, and
processes required by enterprise IT teams, Salesforce, Apple, Google, and
Microsoft.
Our Chief Technology Officer takes security seriously, building safeguards into
every feature and every application so as to comply with your most sought-after
standards, regulations, and certifications. Questions? See the last page.
application.
Cloud Based Architecture — AWS
Veloxy is built on the latest cloud-based architecture using industry standard
services and technologies. Our platform is not hosted in our Pleasanton,
California office. Veloxy hosts its product architecture on the most secure
private cloud offered by Amazon Web Services.
We chose Amazon Web Services because it satisfies the most compliance
requirements for our customers, including PCI-DSS, HIPAA/HITECH, FedRAMP,
GDPR and more. More information can be accessed here: AWS Compliance
application.
Best Practices in Security, Data & Authentication
Encrypted Sessions: All data transmitted between the client and the host is
encrypted, especially log-in credentials and Salesforce data.
Strong Authentication: The identity of all users and their respective devices is
verified using multiple mutually-independent factors.
Oauth 2.0 Client Access Protocols: This is used to support user authorization to
Salesforce, Microsoft, Google, and Apple products. Credentials are not stored.
Source Code Hardening: Any and all programming vulnerabilities are
systematically removed and prevented in realtime.
application.
Clean Data Principles: To sustain accurate Sales AI algorithms, we constantly
remove or fix incorrect, corrupted, duplicate, and incomplete data.
Multi Layered Security Credentials: We protect your internet security with
several security measures, such as prevention, detection, response, and recovery.
AWS Load Balancer Secure Endpoint: LB Secured using SHA-256 with RSA
Encryption.
IP Address Range Lockdown: Access to servers are locked down by IP addresses
and security keys.
Certificate Verification: Verified by GoDaddy Secure Certificate Authority.
Secure Access.
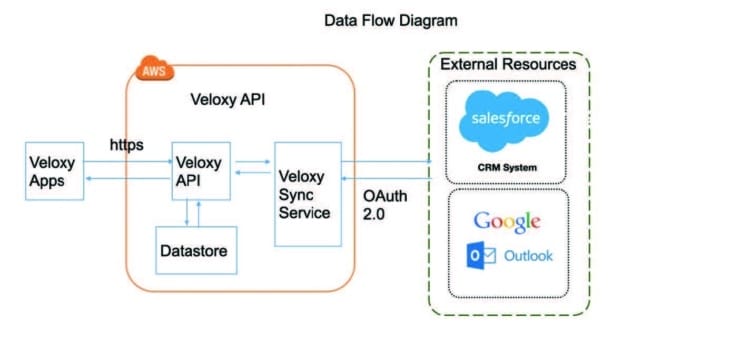
Veloxy Data Flow Diagram
Security Review - Salesforce
Veloxy has been a Certified Salesforce Partner and a publically listed Salesforce
AppExchange App since 2015. We’ve passed all of Salesforce’s security review
tests for over 7 years, proving to them and their customers that we take
customer data protection very seriously.
Salesforce Security Review Teams test Veloxy with threat-modeling profiles
based on the most common and current web vulnerabilities. Our programmed
security defenses repel all of their team’s attempts to attack and manipulate
customer data.
We always pass the following tests and more:
- SOQL and SQL injection
- Cross-site scripting
- Nonsecure authentication and access control protocols
- Vulnerabilities specific to the Salesforce platform, eg. record-sharing
Salesforce has always upheld the highest of security standards for applications
with an AppExchange presence. That is why many of their security reviews are
random and unscheduled—keeping application owners on their toes.
application.

Security Review - Microsoft
Veloxy carries a Microsoft 365 Certification. This designation demonstrates to
Microsoft customers that our platform has consistently passed a test against the
strongest data security and compliance practices and controls from industry
standard frameworks.
The first phase of assessment, attestation, focuses on Veloxy’s security, data
handling, and compliance attributes. When Veloxy is activated in your
organization’s Microsoft 365 platform, the test analyzes the following:
- Data handling
- Security (ie. protocols, processes, procedures)
- Compliance
- Privacy
- Idenity management
The second phase of assessment, certification, performs a thorough security
audit of the Veloxy platform and its overall infrastructure. Here is a sample of
the security controls that Veloxy is constantly vetted against:
- SOC 2
- PCI DSS
- ISO 27001
Veloxy has passed all of Microsoft’s security assessments. Participation is optional,
however, Veloxy constantly participates and receives certification from
Microsoft to ensure customers that their customer data is safe.
Security Review - Google Chrome Store & Google Play
Veloxy is compliant with Google’s Chrome Web Store and Google Play Developer
Program Policies. As required, Veloxy has posted its Privacy Policy on its Chrome
Web Store page, specifying that it will not collect, use, sell, or transfer your data
outside of user-approved use cases. Furthermore, Veloxy is compliant with
Google Play’s user data policies for protecting privacy.
Google Chrome Store requirements supported by Veloxy:
- Two step verification
- Single purpose application
- Publication of up-to-date Privacy Policy on Chrome Web Store
- Handle all user data securley using modern cryptography
Google Play requirements supported by Veloxy [more here]:
- Data and file: all data is stored in the app’s internal storage, no personal
user data is logged to the system log, app uses biometric authentication. - Networking: all network traffic is sent over SSL.
- Cryptography: the app uses strong cryptographic algorithms and a
random number generator, and does not use custom algorithms.
With well over 100,000 extensions, Google takes measures to protect users by
randomly auditing and removing non-compliant applications (Google is not
obligated to monitor the applications), and they do not permit extensions or apps
with obfuscated code. Further, Veloxy abides by the Google APIs Terms of
Service and User Data Policy.
Security Review - Apple
Veloxy complies with all of Apple’s data security, software, and privacy
requirements.
We have implemented and continue to implement new security measures to
ensure the proper handling of all user information collected on Apple devices.
Third parties are prevented from accessing or using any and all user information.
Veloxy works diligently to keep its platform up-to-date with the most recent
Apple OS. Our platform adheres to Apple’s request to be self-contained,
eliminating the need to read or write data outside of the designated container
area, nor downloading, installing, or executing code which changes the Veloxy
app or other apps.
Apple finds user privacy to be their number one priority in the App Store. Veloxy
complies with all of Apple’s recommended privacy best practices [found here].
Veloxy has publised their privacy policy on their App Store page, as required by
Apple.
Applications that are found on random inspection to be out of compliance with
Apple’s Safety, Performance, Business, Design, Privacy and/or other Legal
requirements may be removed from the App Store with or without notice. Veloxy
has never been notified or removed from Apple’s App Store due to our diligent
adherence to Apple’s protocols and users’ right to privacy.
Privacy Policy
The privacy of your data is one of Veloxy’s foundational building blocks. Our
lengthy Privacy Policy [found here] offers full transparency on how Veloxy
collects and uses your information. Your data is only used to deliver the full suite
of benefits found in Veloxy and your chosen integrated applications and devices.
Veloxy will never share or sell your information.
Once you become a Veloxy user, we will retain your data until you choose to
deactivate your account. Once you choose to deactivate your account, and
depending on the nature of your data, records will be removed instantaneously
unless another fixed period of time is agreed upon between you and Veloxy.
Veloxy enables its users with the necessary features to achieve CAN-SPAM, GDPR,
CCPA, and CASL compliance requirements. We are not held responsible when
users perform compliance work arounds.
Social Media Intelligence
Veloxy sales intelligence features contain occasional integrations with social
media platforms, especially LinkedIn and Twitter. To help our users with
centralization of intelligence, Veloxy will place a cookie that tracks social media
data.
Security Detail Request
Sauvik Sarkar is Veloxy’s Co-founder and Chief Technology Officer. With over 17
years of technical experience at eBay, Apple, and other enterprise organizations,
Sauvik is focused on addressing your unique security and data concerns.
If you have very specific questions regarding Veloxy’s platform, integrations, or
security and data policies, please reach out to Sauvik directly at sauvik@veloxy.io,
or you can schedule time on his calendar here: https://calendly.com/sauvik-veloxy